Hey there, cyber warriors and digital defenders! Let’s dive into the intriguing world of vulnerability assessments, where we’ll uncover the secrets of safeguarding your digital goodies while having a few laughs along the way. After all, who said cybersecurity had to be all doom and gloom, right?
Safeguarding Digital Assets through Vulnerability Assessments
Picture this: the digital age, where technology rules and cyber threats are as common as your morning cup of coffee. With hackers and malware prowling the cyber jungles, it’s time for action-packed cybersecurity heroics! Enter vulnerability assessments – the caped crusaders of the digital realm. These assessments are like getting a cyber health checkup for your systems and ensuring they’re not catching any “digital colds.”
The Evolution of Cyber Threats
Okay, so we live in a world where even your toaster might have a secret vendetta against you. Cyber threats are evolving faster than your favorite TV show plot twists. But fear not! Vulnerability assessments are here to save the day, helping us outwit those sneaky attackers and seal off their secret entrances into our digital fortresses.
The Cat-and-Mouse Game of Cybersecurity
Think of cybersecurity as a fancy game of hide and seek, with the good guys (that’s you) trying to outsmart the bad guys (cue the spooky music). As hackers invent new tricks, our cybersecurity defenses need to level up. Vulnerability assessments are like our secret weapon in this battle – they help us stay one step ahead by spotting those weak points and turning them into Fort Knox-level security.
Exploring the Spectrum of Vulnerability Assessment Types
Hold onto your cyberhats, folks, because it’s time to explore the different flavors of vulnerability assessments. Think of them as the different characters in your favorite movie – each with their unique superpowers!
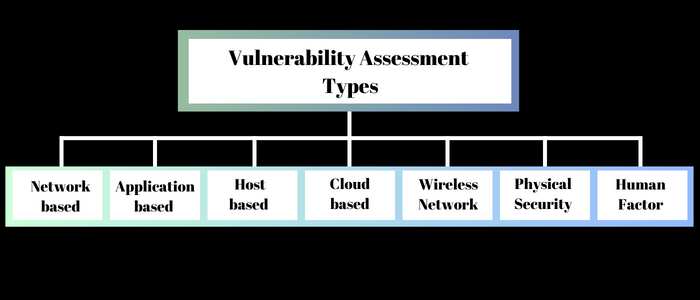
A. Network-based Vulnerability Assessment: Ah, the Sherlock Holmes of cybersecurity! Network-based Assessments are like digital detectives scanning every nook and cranny of your digital playground. They uncover those open doors and windows sneaky hackers might use to waltz right in. Think of it as a high-tech game of hide-and-seek, where we always want the hackers to lose!
B. Application-based Vulnerability Assessment: We’re diving deep into the Matrix with application-based assessments. These assessments are like dissecting your software’s DNA, finding those hidden codes that could turn into vulnerabilities. And then, we go a step further – we simulate real attacks to see if those vulnerabilities could spell trouble. It’s like giving your software a black belt in cyber self-defense.
C. Host-based Vulnerability Assessment: Say hello to the bouncers of the digital club – host-based assessments. They look closely at individual systems, ensuring no gatecrashers can slip in unnoticed. It’s like giving each of your digital guests a friendly pat-down before they enter the party!
D. Cloud-based Vulnerability Assessment: So, we’ve moved to the cloud – exciting, right? But there’s a catch. Cloud-based assessments are like our guardian angels in the sky. They check if our cloud homes are locked tight, ensuring no digital burglars can break in and steal our cloud cookies.
E. Wireless Network Vulnerability Assessment: Wi-Fi – the unsung hero of our digital lives. But even heroes need a reality check. Wireless network assessments are like those tough love coaches checking our Wi-Fi for signs of weakness. Because in the cyber world, weak Wi-Fi is like leaving your front door open for hackers!
F. Physical Security Vulnerability Assessment: Wait, what? We’re talking about actual doors, walls, and security guards now? Yep, physical security assessments are like the bodyguards of the digital realm. They ensure that the walls around our digital treasures are as strong as our passwords.
G. Human Factor Vulnerability Assessment: Okay, folks, we’ve saved the best for last – the one that involves all of us! Human factor assessments are like the cyber survival training we all need. They help us spot phishing emails, avoid traps, and become the Chuck Norrises of the cyber world. Who needs a cape when you’ve got cyber street smarts?
Taking Vulnerability Assessments to the Next Level
Hold onto your keyboards, cyber adventurers, because we’re not done yet! We’ve covered the fundamentals of vulnerability assessments, but now it’s time to take things to the next level and look at some advanced tactics and intriguing developments.
Ethical Hacking and Bug Bounty Programs
Ever heard of the saying, “If you can’t beat ’em, join ’em?” Well, that’s the idea behind ethical hacking and bug bounty programs. Instead of waiting for the bad guys to find the cracks in your armor, you invite friendly hackers to do it first! These cybersecurity heroes get rewarded for finding vulnerabilities, while you get to patch them up before any real mischief happens. It’s like paying someone to break into your house so you can fix the locks before the real burglars show up!
Continuous Improvement and Learning
Remember when you were a kid and your parents said, “You’re never too old to learn”? The same applies to cybersecurity! The digital world keeps changing, and new threats like mushrooms appear after a rainy day. Vulnerability assessments aren’t a one-time deal but a lifelong commitment to staying ahead of cyber villains. So, embrace that learning spirit because it’s the secret sauce to staying one step ahead of those mischievous hackers.
The Path Forward: A Resilient Future
Picture this: a world where cyber threats are as harmless as rubber duckies in a bathtub. Sounds like a dream, right? Well, that’s the kind of future vulnerability assessments we are working toward. By identifying and squashing vulnerabilities today, we’re building a stronger tomorrow. It’s like planting trees that’ll grow into unbreakable cyber fortresses, shading us from even the most relentless cyberstorms.
A Collaborative Effort
Ladies and gentlemen, boys and girls, vulnerability assessments are not a solo performance; they’re a grand symphony requiring every orchestra player. Everyone plays a part in this digital defense dance, from the CEO setting the cybersecurity tone to the end-users clicking away on their devices. It’s like a potluck dinner, where everyone brings their unique dish to create a cybersecurity feast that no hacker
can resist.
The Everlasting Journey
If you thought vulnerability assessments were a one-hit wonder, think again. Cybersecurity is like a thrilling series with a new episode every day. New technologies bring new vulnerabilities, and hackers keep inventing new tricks. But fear not! Armed with the insights from vulnerability assessments, you’re ready for anything. It’s a journey where you emerge as the cybersecurity hero of your own story.
Embracing the Power of Vulnerability Assessments: A Final Word
Let’s pause and soak in the cyber wisdom we’ve gathered. Vulnerability assessments aren’t just about ticking boxes on a cybersecurity checklist; they’re about empowering yourself to take charge of your digital destiny. From networks to applications, from the cloud to the hearts and minds of your team, vulnerability assessments have your back.
A Resilient Digital Future
Imagine a world where cyber threats are mere shadows, unable to touch your digital sanctuaries. That’s the vision vulnerability assessments offer – a resilient digital future where you and your organization can thrive without constantly looking over your virtual shoulder. By embracing vulnerability assessments, you’re putting on the armor of knowledge and strategy to face the unknown confidently.
A Unified Front
Remember when your parents said, “Teamwork makes the dream work”? They weren’t kidding! Vulnerability assessments are like the Avengers assembling against cyber threats. When you combine different assessment types – network, application, host, cloud, wireless, physical, and human-centric – you’re creating an impenetrable force field that leaves hackers confused.
The Beauty of Preparedness
Think of vulnerability assessments as your trusty umbrella on a rainy day. You might not know when the storm will hit, but you’re always ready. In the same way, cyber threats might be unpredictable, but your cybersecurity strategy isn’t. By keeping your vulnerability assessments up to date, you’re always one step ahead of those pesky digital rainclouds.
Thriving in an Interconnected World
We live in an age where our homes, workplaces, and even our fridges are connected to the internet. Vulnerability assessments are your compass in this interconnected wilderness, ensuring that every digital corner is well-lit and protected against lurking dangers.
Champions of Cybersecurity
So, cyber champions, it’s time to wrap up our vulnerability assessment adventure. We’ve laughed, we’ve learned, and we’ve armed ourselves with knowledge that’s worth more than a chest of gold.
“Remember, cybersecurity isn’t just about protecting data; it’s about protecting the future.”
And there you have it, cyber adventurers! We’ve journeyed through the exciting realm of vulnerability assessments, uncovering their secrets, strengths, and potential to transform how we navigate the digital universe. As the world evolves and technology races forward, vulnerability assessments remain our steadfast companions, guiding us through the ever-changing landscapes of cyberspace.
So go forth, armed with the knowledge you’ve gained, and let vulnerability assessments be your guiding light. From networks to clouds, from applications to human behavior, let these assessments be the key to a safer, more secure digital world. And as you champion the cause of cybersecurity, always remember that you’re not alone – you’re part of a global community working together to build a future where digital threats are mere shadows in the past.
Stay curious, stay vigilant, and let vulnerability assessments be the shield that guards against the digital storms. Onward, cyber warriors, to a brighter and more secure digital horizon!

